Table of contents
VoIP technology has transformed businesses’ communication, offering a cost-effective and flexible alternative to traditional telephone lines.
However, VoIP has security risks and threats like any other Internet-based technology.
How does VoIP work?
Voice over Internet Protocol (VoIP) enables the transmission of voice and multimedia.
Unlike traditional telephone lines that use switched circuits, VoIP sends data packets over IP networks.
The basic process of how VoIP works is detailed below:
- Voice-to-data conversion: When you talk on a VoIP phone, your voice is converted into digital signals through a codec (coder-decoder). This process involves digitizing the analog voice signal.
- Packet fragmentation: Digital signals are divided into small data packets. Each packet includes a part of the conversation, information about its destination, and the order in which it should be reassembled.
- Transmission over the network: Data packets are sent over the IP network (such as the Internet or a private network). They can take different routes to reach their destination, thus optimizing network usage.
- Reassembly and conversion: Once the packets reach the recipient, they are reassembled in the correct order and converted back into analog voice signals. It allows the receiver to hear the conversation coherently.
- Delivery: The call is delivered to the recipient’s device, whether a VoIP phone, a computer with VoIP software, or a traditional phone connected to a VoIP adapter.
VoIP operation involves several critical points that must be secured to protect business communications.
Importance of VoIP security
The importance of VoIP security lies in several key factors:
- Confidentiality of information: VoIP calls can contain sensitive and confidential information. Without adequate protection, malicious actors can intercept these communications, resulting in data leaks and corporate espionage.
- Service availability: Attacks such as denial of service (DoS) can render VoIP systems unusable, disrupting business communications and negatively impacting productivity.
- Communications integrity: Attacks can alter or manipulate calls, leading to misunderstandings and poor decisions based on compromised information.
- Regulatory compliance: Many industries are subject to regulations requiring the protection of communications and personal data. Securing VoIP helps to comply with these regulations and avoid legal penalties.
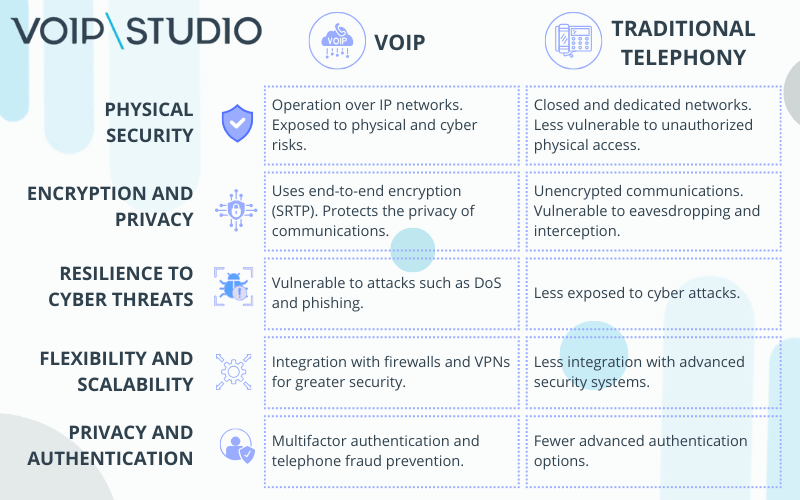
Security differences between traditional telephony systems vs VoIP systems
Main VoIP security threats
While VoIP offers many advantages for business communications, it is critical to be aware of security threats and take proactive steps to protect the system.
Implementing good security practices, educating employees, and using advanced protection technologies can help mitigate these risks and ensure secure communications.
Call interception
Call interception is one of the most significant threats to VoIP security.
This type of attack, also known as “sniffing” or “eavesdropping,” involves an attacker capturing and listening in on conversations in real-time without the participants’ knowledge.
- Prevention: To protect against call interception, end-to-end encryption in VoIP communications is essential. Protocols such as Secure Real-Time Transport Protocol (SRTP) and Transport Layer Security (TLS) ensure that data cannot be read by unauthorized third parties.
Denial of Service (DoS) attacks
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks aim to make VoIP services inaccessible by overloading servers or the network with excessive traffic.
- Prevention: Implementing VoIP-specific firewalls, intrusion detection and prevention systems (IDS/IPS), and quality of service (QoS) controls can help mitigate the effects of DoS attacks. Having contingency plans and redundancies in the network infrastructure is also crucial.
Phishing and Vishing
Phishing and Vishing (voice phishing) are tactics attackers use to trick users into obtaining sensitive information, such as passwords, credit card numbers, or personal data.
- Prevention: Training employees to recognize and handle phishing and vishing attempts is essential. In addition, implementing robust authentication systems and technologies such as call verification can help reduce risk.
Telecom fraud
It includes malicious activities such as stealing VoIP services or making fraudulent calls. It can result in significant costs to businesses.
Types of fraud
– Toll fraud: attackers use VoIP systems to make unpaid long-distance calls.
– Spoofing: originating numbers are spoofed to hide the caller’s identity.
- Prevention: To combat telecom fraud, it is essential to continuously monitor call traffic, establish limits and alerts to detect unusual patterns, and use authentication and encryption solutions. In addition, implementing strict access policies and regularly reviewing system configurations can help prevent unauthorized access.
War dialing
A technique in which attackers use software to automatically dial a range of telephone numbers to find vulnerable VoIP systems or modems connected to data networks. Once a vulnerable system is identified, they can attempt to access it to steal information or disrupt services.
- Prevention: Use robust authentication systems to keep all network-connected devices up to date and monitor incoming traffic and connections for suspicious activity.
Spam over VoIP (SPIT)
Spam over VoIP, known as SPIT (Spam over Internet Telephony), involves the mass sending of unsolicited voice calls, similar to email spam. These calls can be annoying and consume valuable network resources.
- Prevention: Implementing unwanted call filtering and blocking systems and spam detection technologies can help reduce SPIT.
Malware
Malware is malicious software designed to infiltrate, damage, or turn off computer systems. In the VoIP context, it can compromise the security of communication systems by stealing data, intercepting calls, or causing service disruptions.
Common types of malware in VoIP
– Trojans: Hide inside legitimate software and allow unauthorized remote access.
– Ransomware: Encrypts system data and demands a ransom for its release.
– Spyware: Monitors user activities and steals sensitive information.
- Prevention: Keep VoIP software up-to-date and use robust antivirus and anti-malware solutions. Educating employees about safe Internet and email practices and implementing security measures such as access control and network segmentation is also essential.
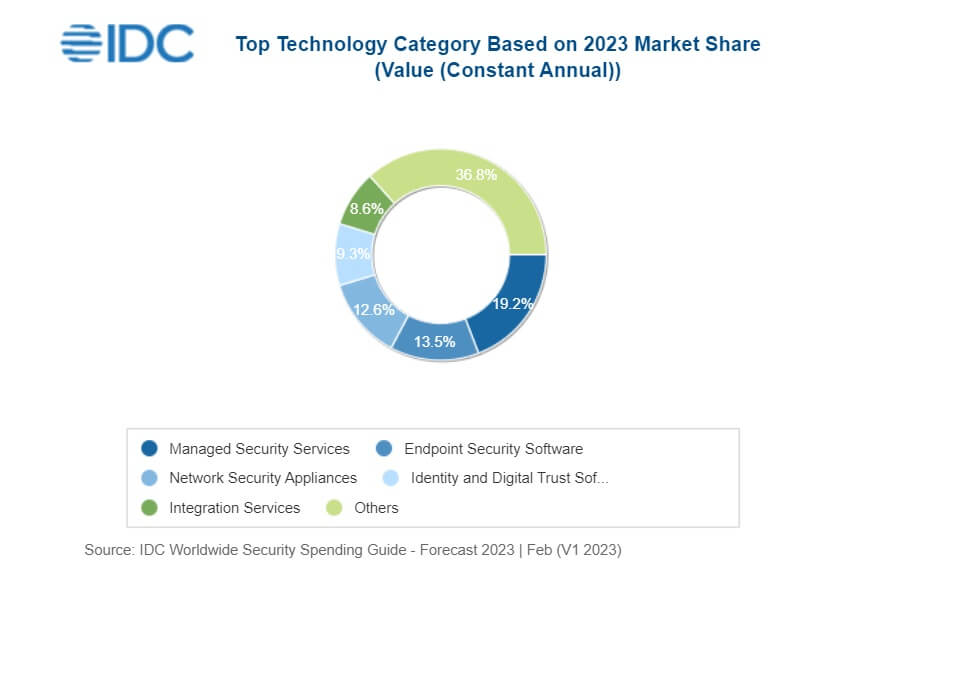
Cybersecurity investment grows exponentially
According to International Data Corporation’s (IDC) Global Security Spending Guide, global spending on security solutions and services will be $219 billion in 2023, an increase of 12.1% compared to 2022.
Investments in cybersecurity-related hardware, software, and services will reach nearly $300 billion by 2026.
The ongoing threat of cyberattacks drives this increase in investment, demands to provide a secure hybrid work environment, and the need to meet data governance and privacy requirements.
Best practices for securing VoIP communications
Enterprises can effectively protect their VoIP systems from various threats and ensure the security and confidentiality of their communications by following these best practices.
Use of encryption on calls
Encryption is essential to protect the confidentiality of VoIP communications. Without it, voice data packets can be intercepted and read by attackers.
- Encryption protocols: Use protocols such as Secure Real-Time Transport Protocol (SRTP) to encrypt voice transmissions and Transport Layer Security (TLS) to protect signaling traffic.
- Implementation: Ensure that all VoIP devices and applications support and use these encryption protocols—Configure systems so that all communications are encrypted by default.
Implementing firewalls and VPNs
Firewalls and virtual private networks (VPNs) are essential to protect the VoIP infrastructure from unauthorized access and attacks.
- Firewalls: Implement VoIP-specific firewalls that can manage and filter voice traffic, allowing only legitimate traffic and blocking unauthorized access attempts.
- VPNs: Use VPNs to encrypt all VoIP traffic between different locations. It is essential for remote workers or branch offices, as a VPN ensures that communications are secure even when using public networks.
Authentication and access control
Strong authentication and access control are vital to prevent unauthorized access to VoIP systems.
- Multi-factor authentication (MFA): Implement MFA to add a layer of security. In addition to passwords, use security tokens, authentication applications, or biometrics to verify user identity.
- Role-Based Access Control (RBAC): Establish policies to ensure that only authorized users can access certain functions or data within the VoIP system. Assign permissions based on job responsibilities and regularly review these assignments.
- 2-Factor Authentication (2FA): Two-factor authentication, also known as two-step authentication, is a security system in which the user is asked to verify their identity in two different ways instead of using only a username and password.
NOTE: If you already have an account with VoIPstudio and want to learn how to implement 2FA authentication, click this link.
Software updates and patches
Keeping your VoIP software up to date is crucial to protect against known vulnerabilities and new threats.
- Regular updates: Configure your systems to receive and apply the latest security updates automatically. It includes VoIP software, operating systems, and other related components.
- Patch management: Implement a patch management plan to ensure that all VoIP applications and devices promptly receive the necessary security patches. Performs tests in controlled environments before patching critical systems to avoid unexpected outages.
Technologies and tools to improve VoIP security
Security protocols (SIP-TLS, SRTP)
These protocols are essential to protect VoIP communications against interception and other attacks.
– SIP-TLS (Session Initiation Protocol-Transport Layer Security)
This protocol encrypts VoIP call establishment and control signals, protecting them against interception and tampering. Using TLS, SIP signals are sent over a secure channel, ensuring that call negotiations and control data are protected.
– SRTP (Secure Real-Time Transport Protocol):
SRTP is an extension of RTP (Real-Time Transport Protocol) that provides encryption, authentication, and replay protection for voice data. This protocol ensures that voice packets cannot be intercepted or altered during transmission.
Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection and Prevention Systems (IDS/IPS) are essential for monitoring and protecting VoIP networks against unauthorized access and malicious activity.
– IDS (Intrusion Detection System)
An IDS monitors network traffic for suspicious activity and possible security breaches. It can generate alerts when anomalous behavior is detected, enabling a rapid response to investigate and mitigate potential threats.
– IPS (Intrusion Prevention System)
An IPS detects suspicious activity and can automatically prevent attacks. This can include blocking malicious traffic, shutting down compromised sessions, and enforcing real-time security policies.
VoIP integration
VoIP-specific IDS/IPS is designed to understand and analyze voice and signaling traffic, detecting and responding to threats specifically targeting communication systems.
Security management solutions
Implementing security management solutions help enterprises implement and maintain a comprehensive and proactive approach to VoIP security.
– Security Information and Event Management Systems (SIEMs)
SIEMs collect and analyze security event data from multiple sources, including VoIP devices, to provide a consolidated view of the organization’s security posture. They facilitate threat detection, incident investigation, and compliance.
– Unified Threat Management (UTM) Platforms
UTM solutions integrate multiple security functions into a single platform, including firewall, IPS, antivirus, web filtering, and VPN. It simplifies security management and provides more comprehensive protection for VoIP systems.
– Monitoring and Auditing
Implementing continuous monitoring and auditing tools helps maintain VoIP systems’ security. These tools can identify vulnerabilities, ensure compliance with security policies, and provide detailed reports on security status.
VoIPstudio, VoIP provider that ensures security in your business communications
We are a VoIP business communications provider that stands out for our focus on security. We apply a series of measures that make VoIPstudio a reliable and secure option for businesses. We are always looking to protect your VoIP communications against threats and vulnerabilities.
Here are several reasons why we ensure secure communications:
Data encryption
We use robust encryption to protect calls and data transmitted over your network.
This includes using secure protocols such as SIP-TLS (Transport Layer Security) and SRTP (Secure Real-time Transport Protocol). It ensures that communications cannot be intercepted or overheard by third parties.
Authentication and authorization
We implement strong authentication and authorization mechanisms to ensure only authorized users can access the system.
It prevents unauthorized access and ensures that users are correctly identified before any activity is allowed.
Secure infrastructure
At VoIPstudio, we maintain a highly secure infrastructure with data centers that meet international security standards.
These data centers have multiple physical and digital protection layers. They include advanced firewalls, intrusion detection and prevention systems, and constant monitoring.
Regulatory compliance
The service complies with various international regulations and security standards, such as GDPR (General Data Protection Regulation). It ensures that personal and business data handling practices are aligned with the strictest best practices and regulations.
Data backup and recovery
VoIPstudio offers data backup and recovery solutions that protect critical information against loss or corruption.
It includes regular backups and disaster recovery plans to minimize the impact of any security incident.
Regular updates and patches
Our platform is kept up-to-date with the latest security patches and updates.
Protecting against emerging vulnerabilities and threats that can compromise system security is crucial.
Continuous monitoring and analysis
VoIPstudio continuously monitors your network and services to quickly detect and respond to suspicious activity or intrusion attempts.
This proactive monitoring allows for the early identification of threats and the implementation of corrective measures before they become serious problems.
Support and security awareness
VoIPstudio also provides support and resources to help its customers understand and apply reasonable security practices in their daily communications. It fosters a security culture throughout the organization.
Discover VoIPstudio, the perfect VoIP business communications solution for your business.
- 30 days free. Try it and be convinced.
- No commitment.
- Unlimited users.
- Includes 200 minutes of calls.
- Free internal calls.
Frequently asked questions and answers on VoIP security
Is it safe to use VoIP for my business communications?
Yes, VoIP can be secure if security measures are correctly implemented. It is crucial to use end-to-end encryption to protect voice and data communications, configure VoIP-specific firewalls, and employ strong authentication and intrusion detection systems to mitigate risks.
What are the main security threats associated with VoIP?
The main threats include call interception, denial of service (DoS) attacks, phishing and Vishing, telecom fraud, and vulnerability to malware and spam over VoIP (SPIT). Implementing security protocols such as SIP-TLS and SRTP, good access management practices, and software updates helps mitigate these threats.
How can I protect my VoIP system against external attacks?
To protect your VoIP system, implement VoIP-specific firewalls, configure VPNs to encrypt traffic, and use advanced security solutions such as IDS/IPS to detect and block intrusion attempts. In addition, be sure to keep all related software up to date and educate users on secure practices.
What security measures are essential to secure VoIP calls?
Strong encryption, such as SRTP, is essential to protect call privacy, configure multi-factor authentication for access to VoIP systems, and implement secure password management policies. In addition, performing regular security audits and rapidly responding to incidents are vital practices.
What additional benefits does VoIP offer in terms of security compared to traditional telephone systems?
VoIP can offer benefits such as integration with IT security systems, monitoring and analyzing traffic in real-time to detect anomalies, and deploying security updates quickly. In addition, VoIP allows the implementation of advanced security measures, as end-to-end encryption and multi-factor authentication, which are more challenging to implement in traditional phone systems.
More from the blog
Want to improve your business communication?
Unlock enterprise-class call center power at affordable prices – no hardware, no delays, no surprises!